Secure your meetings with Mizdah's powerful security features

Mizdah is your best companion in video conferencing. This highly reliable application offers a wide range of features you can enjoy!
The meeting host has access to the following in-meeting security features:
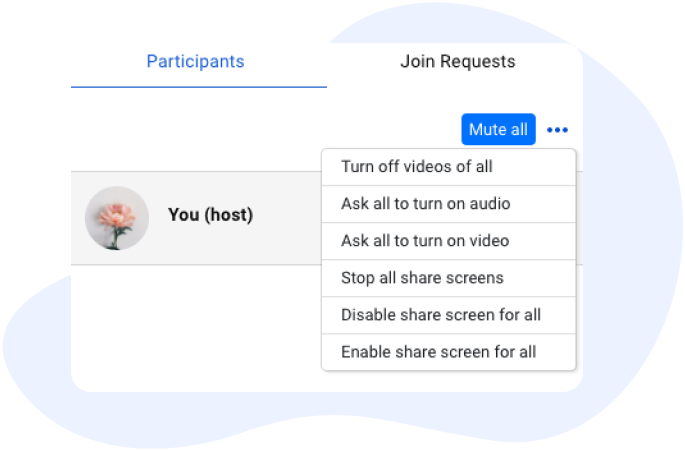
Over the past few years, the idea of data control has gained a lot of attention, particularly in relation to customer data. Consumers are highly concerned about it, and businesses are talking about it more frequently as well.
Mizdah takes the security and privacy of user’s data very seriously. Our engineering and security team has put in place a multi-level security infrastructure to secure the data traveling between client and the server as well as the data that stores in the database.
Mizdah servers are hosted in the AWS cloud and are completely protected by both Ogoul's internal security system and the security infrastructure of the AWS cloud. To safeguard our servers and user data, it also includes anti-virus, anti-spyware, and anti-malware software, Advanced Shield, and other security technologies.
All data communicated between the server and the client apps is fully encrypted with the state of the art encryption and masking technologies. The user data is stored on the server in encrypted form secured with the help of multi-level encryption framework developed by Ogoul Technology.
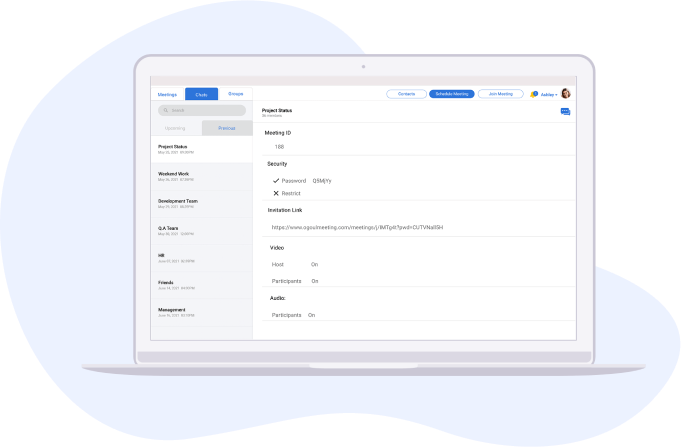
Mizdah gives control back to users to set up a meeting as their heart desires